Communications intelligence (COMINT) systems play a critical role in gathering intelligence from communication channels. They focus on intercepting, processing, and analyzing voice, data, and signals to extract valuable insights. Organizations and governments rely on COMINT systems to ensure security, detect threats, and gain strategic advantages in various operations. To understand their importance, it’s essential to look at their key features and capabilities, which enable efficient information gathering.
Key Points:
- COMINT systems intercept and analyze communication channels.
- They capture voice, data, and other communication signals.
- Governments and organizations use COMINT systems for intelligence purposes.
- They provide critical support in threat detection and security efforts.
- Advanced features enable precise data processing and analysis.
What Are COMINT Systems?

COMINT systems, used widely in the intelligence community, focus on communication interception. They capture voice, radio, and data signals from targeted sources, allowing detailed analysis of the content. By monitoring such channels, governments and defense organizations can detect and neutralize potential threats, making them invaluable in national security.
Systems like these enable authorities to gather sensitive information without alerting the target. Many COMINT systems integrate with broader SIGINT (Signals Intelligence) platforms. This integration ensures that the intercepted data can be shared and analyzed alongside other intelligence sources. By combining different intelligence types, analysts can form a more comprehensive understanding of the situation.
Key Features
Signal Interception
A core function of COMINT systems is signal interception. They capture communication signals from various sources, including radio, satellite, and digital transmissions. By intercepting these signals, the system extracts essential data, which analysts can further process to gather intelligence.
Wide Range of Frequencies
Covering a broad spectrum of frequencies enables the capture of signals across different mediums and sources, from military radio communication to civilian telecommunication networks. The ability to monitor a wide frequency range ensures that no critical communication is missed.
Real-Time Data Processing
They have the capacity to process intercepted data instantly, allowing analysts to act quickly on the information received. Speed is essential in many scenarios, such as military operations or urgent security threats.
Advanced Signal Analysis
They often incorporate advanced signal analysis tools. These features allow them to identify patterns, classify different types of signals, and determine the location or identity of the source. This is particularly useful in distinguishing between friendly and hostile signals.
Capabilities that Make COMINT Systems Essential
Communication Decryption

Encryption is a significant obstacle in intelligence gathering. COMINT systems have decryption capabilities to break through encrypted communications. By decoding secure channels, they provide access to critical data that would otherwise remain hidden.
Targeted Monitoring
COMINT systems offer precise targeting. By focusing on specific communication channels or individuals, they minimize unnecessary data collection. This focused approach ensures more relevant and actionable intelligence.
Remote Signal Collection
They can operate remotely, capturing signals from distant or inaccessible locations. This allows intelligence agencies to monitor communication activities from virtually anywhere in the world, providing a strategic advantage in monitoring adversaries.
Automated Data Filtering
Automated features allow filtering out unnecessary data. The ability to sort through vast amounts of information quickly ensures that only relevant data reaches the analysts. This streamlining significantly speeds up the analysis process.
High-Level Encryption Techniques
To counter evolving encryption techniques used by adversaries, COMINT systems continually upgrade their decryption methods. This capability is essential in gaining access to high-level communications that would otherwise be shielded.
COMINT Systems in Defense and Security

The role of COMINT systems extends across many defense and security sectors. Military operations benefit from the interception of enemy communications, providing real-time updates on enemy movements, strategies, and vulnerabilities. These systems help detect potential attacks, safeguarding key infrastructures and personnel.
Additionally, law enforcement agencies use them in counter-terrorism efforts, intercepting criminal communication networks. By monitoring such networks, authorities can intervene in planned attacks or criminal activities. Without the precision and advanced capabilities of COMINT systems, many of these operations would be hindered.
Challenges Faced by COMINT Systems
Evolving Communication Technologies
As technology advances, so do the methods used by adversaries to communicate. The shift from traditional radio communications to encrypted digital channels presents a growing challenge. COMINT systems must constantly evolve to keep pace with these changes.
Data Overload
As communications occur across multiple channels and platforms, the systems capture vast amounts of information in real-time. Automated tools help by filtering out irrelevant or redundant data, but the remaining data still requires careful examination. Without this automated sorting, analysts would face an overwhelming task, as the raw data often contains a mix of important intelligence and insignificant noise. The complexity and volume of the information demand skilled human intervention.
Privacy Concerns
In an era of heightened concern over personal privacy, the use of COMINT systems raises ethical questions. The line between national security and individual privacy is often blurred. Governments and organizations must ensure that the use of these systems complies with legal and ethical standards.
Encryption Techniques
Advanced encryption is another major obstacle. As adversaries use more sophisticated encryption, COMINT systems must constantly upgrade their capabilities to stay ahead. Failure to do so could result in critical intelligence slipping through undetected.
COMINT Systems as a Key Tool in National Security
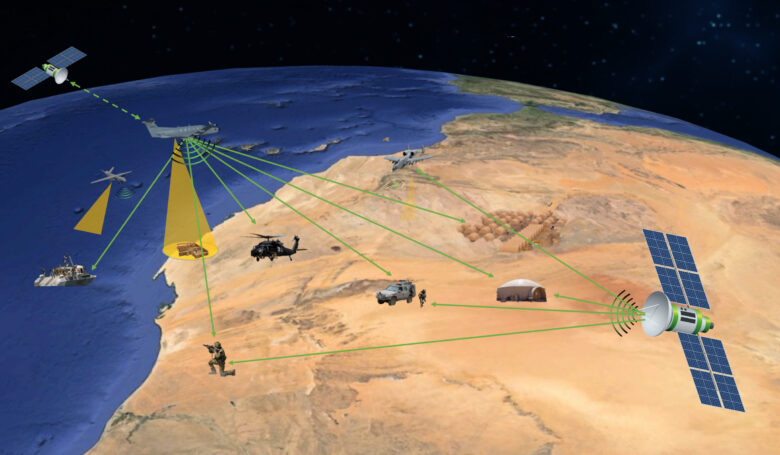
The importance of these systems cannot be overstated in modern intelligence efforts. They provide unparalleled access to communication channels that would otherwise remain hidden. Their advanced capabilities in signal interception, decryption, and real-time analysis make them invaluable tools in national security and defense.
The continuous evolution of COMINT systems will ensure that governments and organizations stay ahead of adversaries. By keeping pace with advances in communication technology and encryption, COMINT systems will remain a critical asset in the intelligence arsenal.
Conclusion
COMINT systems play an essential role in ensuring security across a range of sectors, from military operations to counter-terrorism. Their ability to intercept and analyze communications offers a significant advantage in intelligence gathering. As technology evolves, so too must the capabilities of COMINT systems to meet new challenges.
For those working in intelligence or security, staying informed about the latest advancements is crucial. Their role in securing sensitive information and countering threats makes them indispensable in the modern world.

